In the early days of smart contracts, issues like double-executions, re-entrancy, and unchecked state changes often slipped into production. While security practices and AI-driven auditing tools now catch these problems more easily, unintended duplicate actions can still creep into modern code—especially in contracts with modular designs or cross-contract interactions.
One subtle but impactful example is duplicate fee deductions. Consider this scenario:
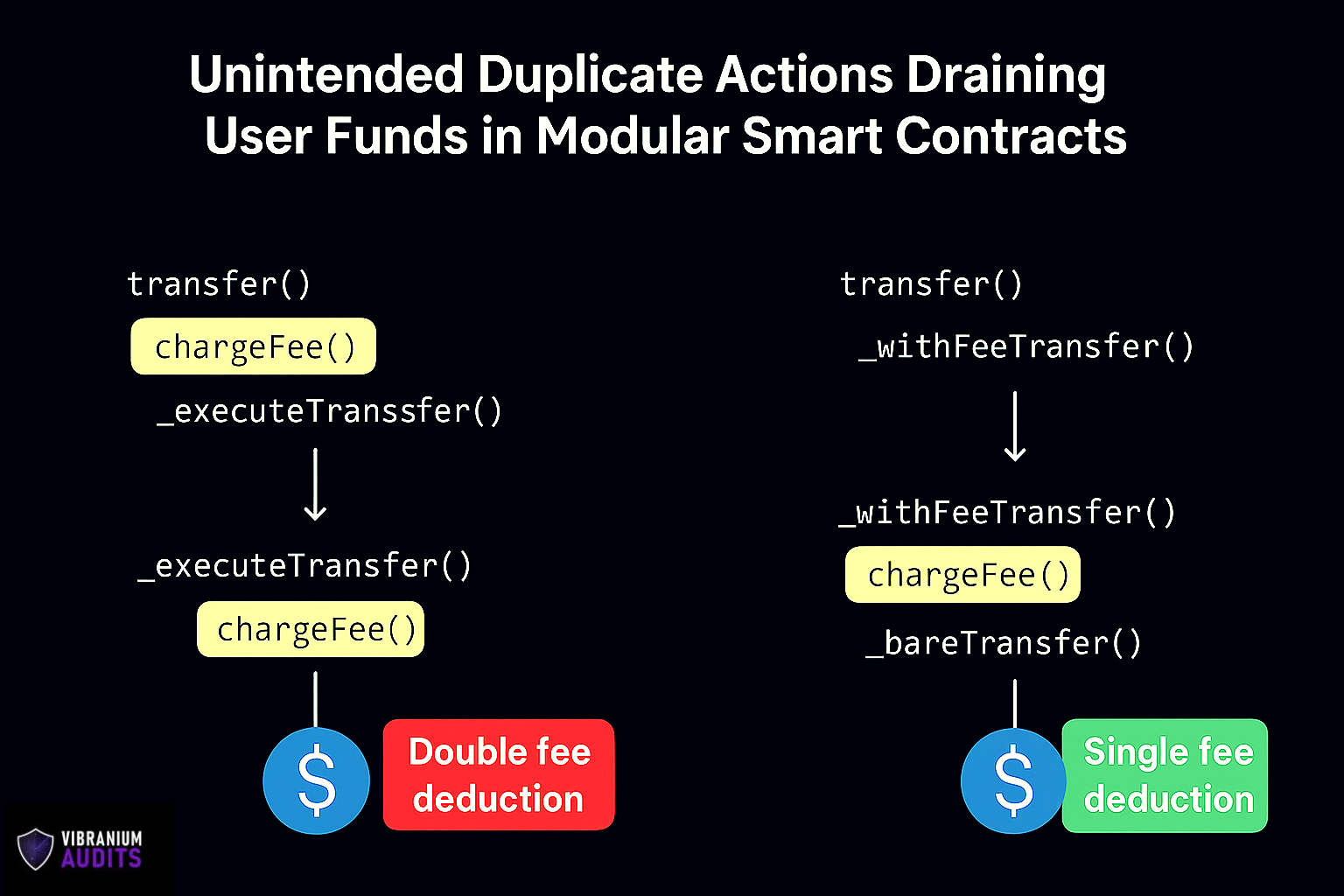
1. A contract’s transfer() function deducts a transaction fee by calling _chargeFee().
2. After deducting the fee, it delegates the core logic to _executeTransfer().
3. Unfortunately, _executeTransfer() also contains a call to _chargeFee().
The result? The sender’s balance is charged twice for the same transaction. Instead of paying the intended fee once, the user is overcharged—potentially draining funds much faster than expected.
This issue isn’t just theoretical. In modular function design, developers often split responsibilities across multiple functions for clarity and reuse. But if state-changing operations like fee deductions, burns, or balance updates are triggered in more than one layer, duplication can occur. In complex scopes with internal functions reused for different flows, the risk only grows.
Why This Happens
1. Improper state tracking: Developers assume a fee has only been charged once, without checking call paths.
2. Function reuse pitfalls: Internal functions are written for multiple purposes, but not all use cases require repeated actions.
3. Lack of invariants: No safeguards exist to assert that critical financial actions happen only once per operation.
How to Prevent It
1. Map out execution flows – Document how funds move across internal and external calls.
2. Isolate financial logic – Dedicate single, unambiguous functions to handle critical state changes.
3. Use clear naming – Functions like _withFeeTransfer() or _bareTransfer() make intentions explicit.
3. Leverage AI & static analysis – Modern auditing tools can flag duplicate state changes automatically.
4. Add invariants in tests – Assert that balances before and after transfers match expectations with a single fee applied.
Closing Thoughts
Unintended duplicate actions may sound like an issue from the past, but modular contract design means they can resurface in subtle ways. By carefully tracking where financial state changes occur—and ensuring they happen once and only once—developers can prevent costly mistakes that compromise user trust.